- Pirates as IT staff use NFT projects, flying nearly a million dollars.
- North Korean groups are behind 70% of cryptographic flights in 2025, including bybit’s piracy of $ 1.5 billion.
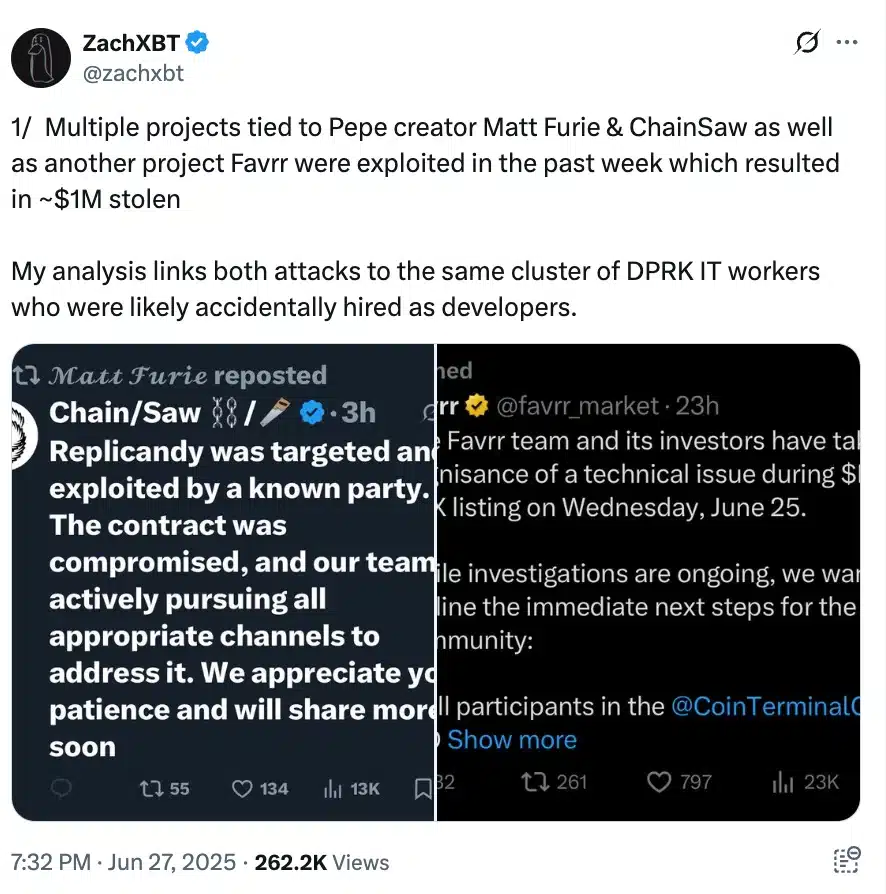
A new wave of crypto exploits has shaken the web3 space, while hackers who have the identity of computer staff have successfully infiltrated several collections of NFT linked to the creator of Pepe Matt Furie and left with nearly a million dollars in stolen active ingredients.
Web projects attacked and losses suffered
According to the analyst of the Zackxbt channel, these attackers acquired access to the initiate to projects such as Favrr, Replicandy and Chainsaw, among others, by posing as legitimate technological workers.

Source: ZACHXBT / X
Once inside, they manipulated the NFT striking systems to generate large lots of chips, unloaded them on a large scale and triggered a collapse of market value.
The exploitation has not only drained funds but also destabilized affected ecosystems, exposing serious vulnerabilities in internal access control and project security.
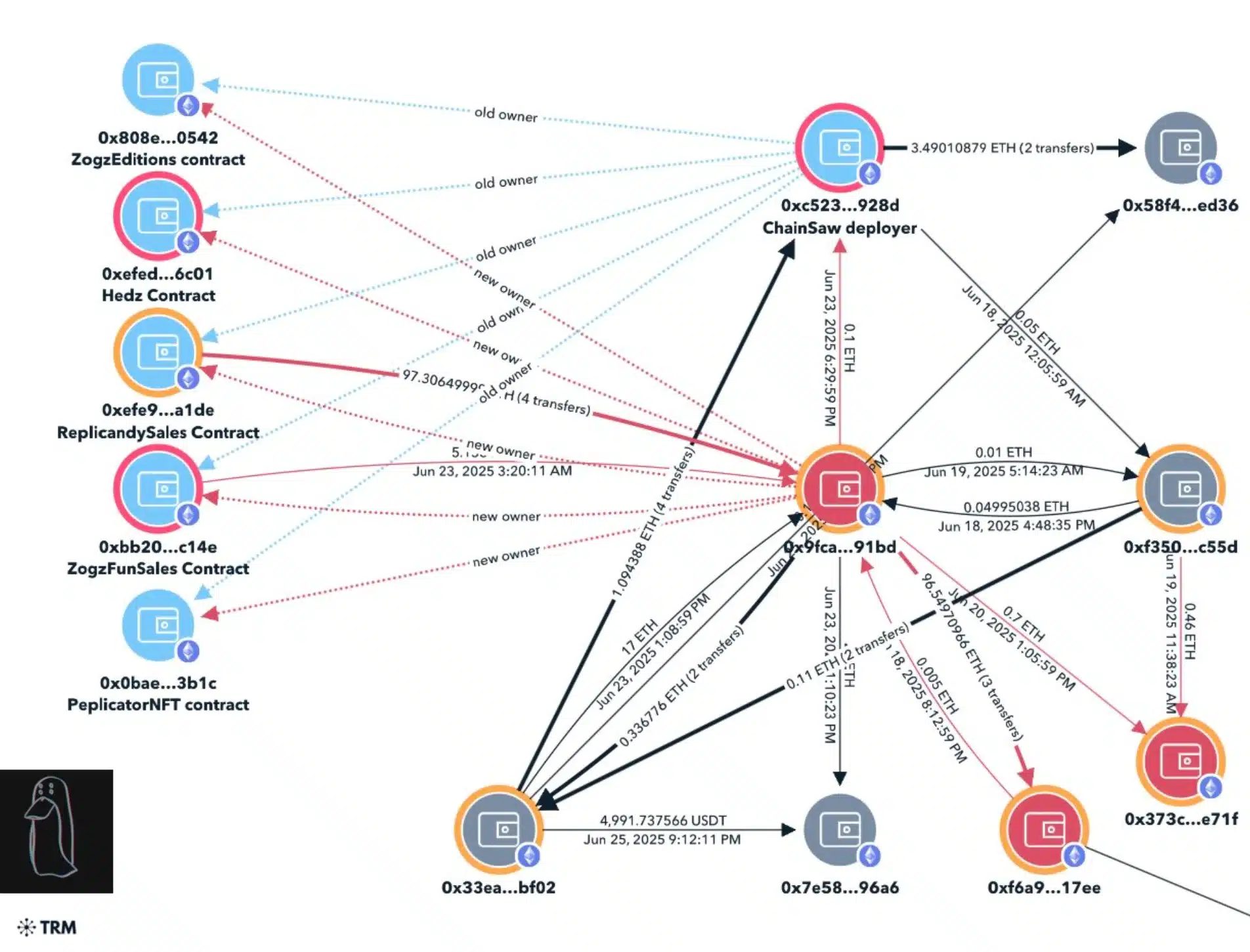
The calendar of the exploit of replicas reveals a methodically executed violation, with strong indicators connecting it to the North Korean computer agents.
How was the hack made?
On June 18, the ownership of the replica contract was discreetly transferred to a new address (0x9fca), which then removed the mint product and resumed the strike, ultimately crushing the soil price by flooding the NFT market.

Source: ZACHXBT / X
This scheme was again repeated on June 23 with additional collections, Peplicator, Hedz and Zogz, causing greater devaluation and losses totaling more than $ 310,000.
The chain analysis has retraced the stolen funds through several portfolios, finally discovering the USDT deposits channeled towards Mexc and identifying two suspect Github developers’ accounts – “Devmad119” and “SUJITB2114”, linked to violation.
Internal newspapers have further exposed inconsistencies, such as developers claiming to be based on the United States while using Korean language parameters, time zones in Asia / Russia and Astral VPN.
These red flags strongly suggest that the attackers were part of a coordinated North Korean campaign operating the lax verification procedures in web3 hiring.
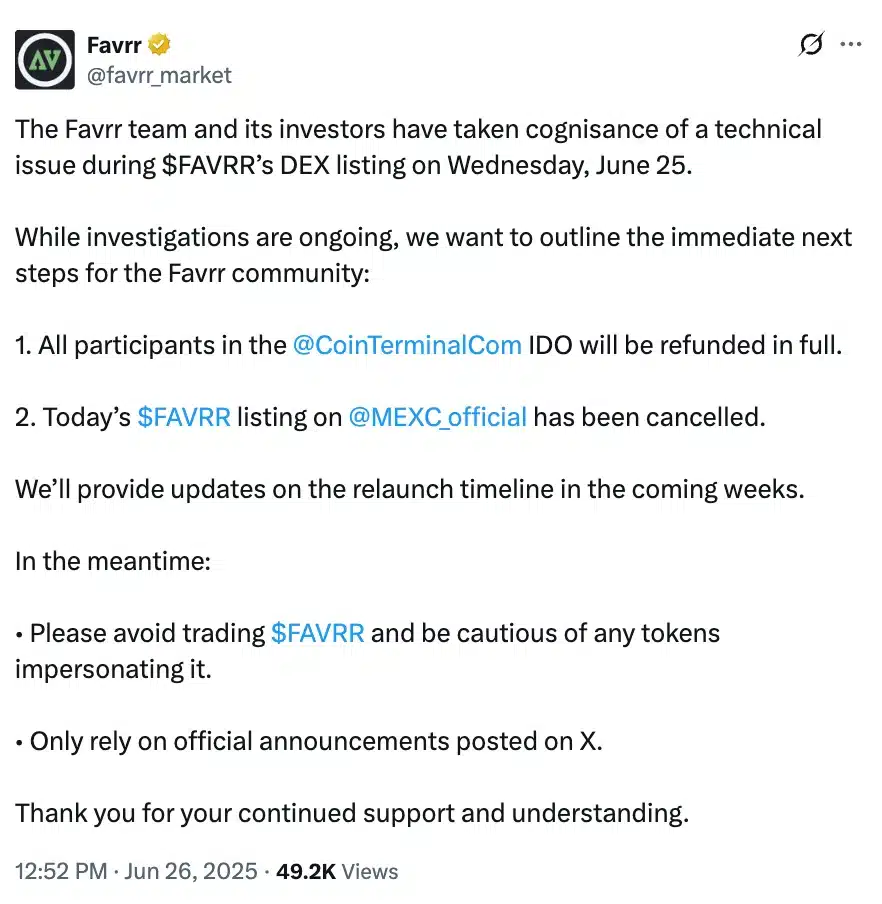
While the FAVRR team responded quickly with improved user safety measures, Chainsaw did not issue a brief warning and then deleted it.

Source: Tavrr / x
On the other hand, Matt Furie remained completely silent, suggesting that the wider image points to a much more disturbing reality.
The rise of North Korean pirates
That said, north Korean hackers became increasingly aggressive in 2025, researchers attributing more than $ 1.6 billion, or about 70% of all stolen crypto this year, to state-affiliated groups.
The amazing violation of $ 1.5 billion in February, now considered their work, is the largest cryptographic flight in history.
These actors, notably the famous group of Grazillants Ruby, extended their scope beyond the crypto, previously infiltrating American defense entrepreneurs and now targeting IT companies thanks to false hiring campaigns and elaborate social engineering tactics.
In response to the growing wave of fraud linked to crypto and security offenses, nations around the world intensify regulatory guarantees.
In the United States, the Trump administration actively increases a series of pro-Crypto policies designed to protect the industry from discriminatory banking practices and excessive regulatory pressure.
This is in particular an executive decree pending to prohibit financial institutions from targeting crypto companies, efforts to make the restrictions imposed by the SEC and a legislative restriction, and legislative support for managers such as the Act on Engineering to clarify the rules for staboins and digital assets.
Meanwhile, Australia has moved quickly to tackle impaired ATM by placing cash transactions at $ 5,000 to the strict identity checks and requiring real -time scam warnings.
Together, these measures reflect an international change coordinated to a more secure and more responsible web3 environment.

