Wallets linked to the notorious attacker “Blockchain Bandit” have reportedly become active after being inactive for more than five years.
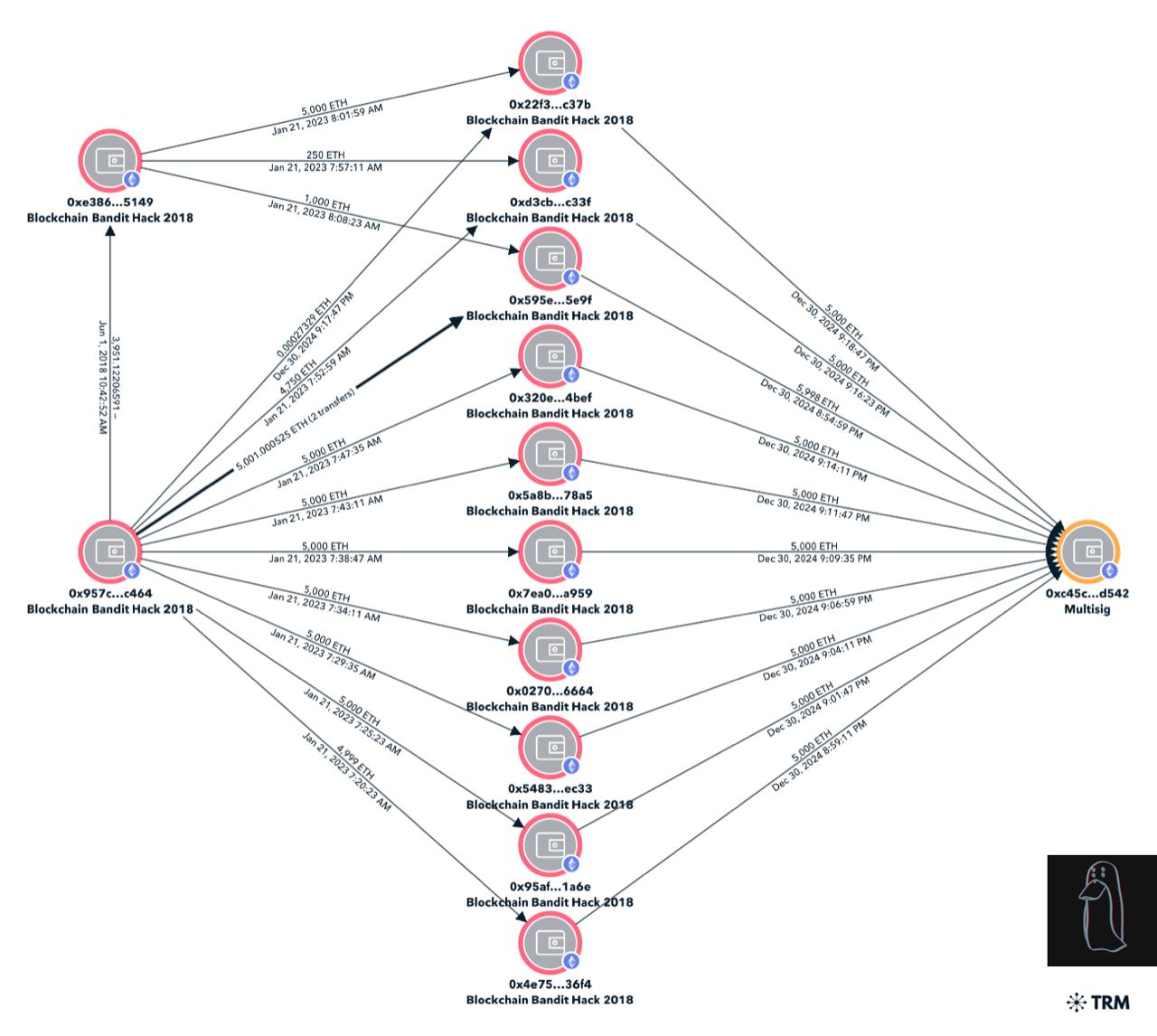
According to crypto investigator ZachXBT, the attacker bundled 51,000 ETH worth over $172 million from 10 different wallets into a single multi-signature wallet.
Who is the Blockchain Bandit hacker?
ZachXBT’s analysis showed that the 10 wallet addresses used in today’s transfer were last active in 2018. This means that the attacker decided to access these funds for the first time since more than five years.
So, who is this Blockchain Bandit? For those new to cryptography, this is probably an unfamiliar name. However, for long-term crypto enthusiasts, it was one of the most captivating and concerning names in 2018.
The infamous “Blockchain bandit“ is the pseudonym of an attacker who systematically exploited weak private keys on the Ethereum blockchain to steal cryptocurrency. It became popular by simply guessing the private keys of several vulnerable wallets and stealing millions of funds.
The attacker scanned the Ethereum network for wallets secured by weak, non-random, or poorly generated private keys. These keys were often the result of programming errors or faulty implementations of cryptographic libraries.
The Blockchain Bandit used automated scripts to search the blockchain for vulnerable addresses. When a weak key was identified, the attacker quickly transferred funds from the wallet to his own address. In most cases, it took several days before the owner realized the theft.
In total, the hacker was able to steal over 50,000 ETH using this simple technique from over 10,000 wallets. The name “Blockchain Bandit” comes from a 2019 WIRED feature that revealed the pattern of this attack.
Meanwhile, a security analyst named Adrian Bednarek identified how the bandit used a pre-generated list of keys to automate the scan and withdraw funds from vulnerable wallets in seconds.
“You see, on Ethereum, private keys are 256-bit numbers. Brute forcing is basically impossible. But some wallets used terrible random number generators, creating weak private keys. Think: password123 or an empty recovery phrase. One key was literally… “1”. The Bandit didn’t just target bad private keys. He also exploited: weak passphrase-based wallets (like “Brainwallets”) and misconfigured Ethereum nodes. His approach made him almost unstoppable,” wrote Web3 analyst Pix.
Why is the attacker active again after five years?
Although these particular wallets became active today for the first time since 2018, some of the other wallets were used to transfer funds in January 2023 and purchase Bitcoin.
Nonetheless, today’s transfer marks the largest consolidation of all ETH funds stolen from the attacker. This could indicate several things.
First, moving funds to a multi-signature wallet could indicate that the attacker is preparing for a large transaction or series of transactions. This may include laundering funds through mixers, decentralized exchanges, or other tools to disguise their origins.
Furthermore, the consolidation of funds could be a prelude to the liquidation of all or part of ETH. Notably, the liquidation of such large quantities of ETH in the current market could raise concerns about the near-term price of Ethereum.
On the other hand, the attacker can anticipate favorable market conditions, such as an ETH price surge, to maximize the value of their stolen holdings during liquidation.
However, the most worrying thing is that consolidated ETH could be used to fund other exploits. For example, funding transaction fees for a new round of attacks or enabling operations on other blockchain networks.
Overall, the possibility of such an infamous hacker becoming active again could be a concern for the crypto space. We have already seen the industry lose $2.3 billion in 2023, a massive 40% increase from 2023. Ethereum was also the hardest hit network among these attacks.
Disclaimer
In accordance with the Trust Project guidelines, BeInCrypto is committed to providing unbiased and transparent reporting. This news article aims to provide accurate and current information. Readers are, however, advised to independently verify the facts and seek professional advice before making any decision based on this content. Please note that our Terms and Conditions, Privacy Policy and Disclaimer have been updated.

